IJCRR - 3(4), April, 2011
Pages: 34-45
Print Article
Download XML Download PDF
PERFORMANCE ANALYSIS OF TCP VARIANTS OVER MANET: IMPROVING RELIABILITY OF MOBILE AD HOC NETWORKS
Author: Mueen Uddin, Aziazah Abdul Rahman
Category: Technology
Abstract:The need of reliable communication, where no data loss, no duplication and no out of order delivery occurs becomes a vital necessity of most application programs in all networks. Transmission control protocol provides error free reliable communication for wired networks. The decision of deployin transmission control protocol in ad hoc network becomes difficult due to the availability of its different variants with Mobile Ad hoc Network routing protocols especially when mobility is an issue. This paper analyzes the advanced and sophisticated transmission control protocol Variants with Ad hoc On-demand Distance Vector routing protocol to measure different parameters required for reliable communication such as the finest performance of packets delivery rate, average end-toend delay, and packet dropping. Finally from various differentiable results, an enhanced combination of transmission control protocol variant Vegas and Ad hoc On-demand Distance Vector routing protocol will be chosen and refined to achieve desirable output. The refinement proves to be the
better solution of deployable protocols of Transmission Control Protocol in Mobile Ad hoc Network with decidedly mobile environment.
Keywords: Mobile Ad hoc Networks; Transmission Control Protocol Variants; Proactive and Reactive Protocols; Network Simulator, Reliability.
Full Text:
1. INTRODUCTION
The glory of communication seems new but actually surrounded by different evolution eras. There were different transformations and trends evolved for the optimization and enhancements of communication styles. Enormous approaches were adopted and became obsolete from time to time as the new technological revolutions had set the communication parameters up-to-date. The whole phenomenon of communication process signifies the importance of reliable and unfailing transportation of data and information from source (sender) to destination (receiver). In this concern of intact data transportation much development of protocols and their improvements yield very progressive results. These results proved the efficient transmission and the reception of intact and undamaged data. Today‘s Information Technology era is working to provide ease and simplicity of procedures intended for the consumers in communication arena. The mobile phone technology is becoming an essential part of life and is accessible to almost everyone. Wireless networks are categorized into structured and non structured networks. Mobile phone technology falls in structured wireless networks, and they require an infrastructure like base stations, transducers, and other intermediate devices for the creation of networks. The other category of wireless networks is unstructured or sometimes called ad hoc wireless networks, being very popular now a day. This paper focuses on how information can be transmitted reliably and timely through wireless ad hoc networks using transmission control protocol Variants as these networks are build-on without relying upon any infrastructure. Reliability is an important issue to be discussed in this paper and will be analyzed by applying different transmission control protocol variants with Mobile Ad hoc Networks to provide a secure, efficient and reliable mechanism for the transmission of packets across the network. To resolve the problem of reliability certain protocols were discussed and in consequence, transmission control protocol was developed with the true answer of reliability in any mode of communication‘s transportation [28]. Due to ease of node such as laptops and palmtops mobility, connections creation and failure are considered as problems between nodes in ad hoc networks and can be resolved by their internal routing protocols. Heavy traffic of data segments between nodes may lead to congestion problems and hence to the reliability of data being transmitted, and this issue is considered as a major issue in data communication and transportation [21]. Transmission control protocol is not well suited for wireless networks since it was developed for wired networks, due to the heavy packet and connection losses especially in Mobile Ad hoc Networks, the performance of transmission control protocol degrades significantly [22]. To overcome these issue and problems, different versions of transmission control protocol called variants were developed especially for wireless ad hoc networks to provide reliable communication. Although there are various routing protocols for route configurations in Mobile Ad hoc Network are available [23], but the problem is the selection of suitable coupling and pairing of transmission control protocol variants and Mobile Ad hoc Network routing protocols to work efficiently altogether to provide a reliable communication.
2. PROBLEM DEFINITION
Transmission control protocol is a reliable and mostly used protocol developed initially for wired networks and performed well in its respective environment [6], but current trends are making a shift from wired to wireless world. Since wireless communication is a lossy in nature and therefore typical transmission control protocol is not well suited in this situation and may cause unwanted delays and packet loss which makes the communication unreliable and erroneous. Another protocol called User Datagram Protocol is being used which performs well in the wireless environments providing error free communication with very low delays [6]. User Datagram Protocol is mostly used in wireless streaming communications, where delays are not affordable instead packet dropping or loss is acceptable than delaying hence reliable communication is not achieved [22]. This paper focuses on reliability as it is achieved through transmission control protocol, so the major concern of this research will be the selection of transmission control protocol variants with Mobile Ad hoc Network routing Protocols to achieve reliability. Interestingly, how this protocol behaves in Mobile Ad hoc Network environment where there are no mobility constraints on nodes. To answer this question, certain related facts need to be pondered, like selection of different transmission control protocol variants, their advantages and disadvantages in collaboration with their corresponding Mobile Ad hoc Network routing protocols and quality of service.
3. RELATED WORK
The related work with the same distinction could be found on the comparison of different transmission control protocol variants with Mobile Ad hoc Network routing protocols in [15, 30]. Several schemes have been proposed to alleviate the effects of non congestion related losses on transmission control protocol performance over networks that have wireless or similar high loss links [14, 28]. Many techniques choose from a variety of mechanisms, such as local retransmissions, split transmission control protocol connections, and forward error correction, to improve end-to-end throughput [25]. The most common problem found in major studies was related with the inability of transmission control protocol to differentiate between link failure and congestion. Beside this, various studies have discussed different comparable scenarios like: energy consumption, static nodes nature, and others in Transmission Control Protocol and Mobile Ad hoc Network environments. But this paper specifically focuses on the mobility in the Mobile Ad hoc Networks. The performance of transmission control protocol will be judged on the basis of random mobility.
4. MOBILE AD HOC NETWORKS
Mobile Ad Hoc Networks are self configured infrastructure less networks formed and deformed abruptly [2]. They cover an extent of applications in multi-hop scenarios, such as in locations of conferencing, hospital, battlefield, rescue, and even home. Their topology is selforganized, dynamic, and decentralized [5]. The network formation depends on the existence of mobile hosts; some of these mobile hosts are willing to forward packets for their neighbours. These networks have no fixed routers; every node could acts as router. All nodes are capable of moving and can be connected dynamically in an arbitrary manner [7]. The responsibilities for organizing and controlling the network are distributed among the terminal themselves. There is no intermediate device required in between the nodes to establish or form a network. Hence the nodes with the help of each other can establish a network and start communication. In this type of network, some pairs of terminals may not be able to communicate directly with each other and have to rely on some other terminals so that the messages are delivered to their destinations. Such networks are often referred to as multi-hop or store-and-forward networks. The nodes of these networks function as routers, which discover and maintain routes to other nodes in the networks. The clarification of Mobile Ad Hoc Networks with transmission control protocol variants is highly structured and discussed in [2, 15, and 16].
4.1 Routing in Mobile Ad Hoc Network: The routing infrastructure in Mobile Ad hoc Networks should be established in a distributed, self-organized way to overcome the issues of node mobility. Different routing protocols have been proposed along with some evaluating work already been done. These protocols are majorly classified into two main categories as Proactive and Reactive [23].
4.1.1 Proactive Routing Protocols: The primary characteristic of proactive approach is that each node in the network maintains a route to every other node in the network all the time [23]. Route creation and maintenance is accomplished through some combination of periodic and event-triggered routing updates. Periodic updates and checking consist of routing information exchanges between nodes at set time intervals. The updates occur at specific intervals, regardless of the mobility and traffic characteristics of the network.
4.1.2 Reactive Routing Protocols: Reactive routing techniques, also called as on-demand routing [2]. Here instead of maintaining the routes periodically, route only maintained when needed by nodes at the time of transmission [23]. Link connectivity can change frequently in ad hoc networks and control overhead is costly. Routes are only discovered when they are actually needed. When a source node needs to send data packets to some destination, it checks its route table to determine whether it has a route; If no route exists, it performs a route discovery i.e. checks available routes from source to destination to find a suitable path to the destination hence, route discovery becomes on-demand. The route discovery typically consists of the network-wide flooding of a request message.
5. PROPOSED WORK
This paper focuses on Ad hoc On Demand Distance Vector routing protocol as a reactive routing protocol for performing different simulation scenarios with various selected and supported transmission control protocol variants to prove an error free and reliable communication. The Ad hoc On-Demand Distance Vector routing protocol is intended for use by mobile nodes in an ad hoc network [24]. It offers quick adaptation to dynamic link conditions, low processing and memory overhead, low network utilization, and determines unicast routes to destinations within the ad hoc network. This algorithm enables dynamic, self-starting, multihop routing between participating mobile nodes wishing to establish and maintain an ad hoc network [23, 32]. It allows mobile nodes to obtain routes quickly for new destinations, and does not require nodes to maintain routes to destinations that are not in active communication. Ad hoc On-Demand Distance Vector routing protocol allows mobile nodes to respond to link breakages and changes in the network topology in a timely manner. When a link is broken due to some erroneous condition, it notifies the affected set of nodes so that they may invalidate the routes using the lost link [2].
6. METHODOLOGY
Network Simulator 2 will be used for performing simulations using different parameters considering mobility. It is a discrete event simulator targeted at most of the networking research [32]. There are various simulation components used by Network Simulator to establish special and diverse simulation scenarios. Among these components most common and important are:
Nodes are the "hardware entities" in a network environment.
- Agents are "software entities" dependant on nodes like transmission control protocol and user datagram protocol.
- Links are used to connect the nodes in the network. Links can be of two types:
I. Simplex can forward packets in one direction only.
II. Duplex can forward and receive packets simultaneously i.e. it can operate in both directions at the same time.
- Traffic generators are the specified nodes which are:
I. Source is an agent which is the originator of packets.
II. Sink is another agent which is the destination for the source packets.
6.1 Simulation Operations: The simulation operations performed by the Network Simulator -2 after employing the components can be broadly categorized as follow:
- Creating the event scheduler: in this operation different event related activities are being done, like create scheduler, schedule events and start scheduler.
- Creating network: in this operation the required nodes with their linkage and queuing operations are created.
- Creating connection: in this operation the actual connection scheme transmission control protocol is given.
- Creating traffic: in this operation traffic flow is being mentioned i.e. how much traffic is needed for the simulated network. The common traffic creation criterion is Constant Bit Rate where constantly bits of traffic are supplied to the network.
- Tracing: this is the crucial operation which reads the simulation generated output file and shows different output results in form of text or graph.
6.2 Procedural Work Flow:
The objective of the research is to analyze transmission control protocol variants such as New-Reno, Sack, and Vegas over Mobile Ad hoc Network routing protocol Ad hoc On-Demand Distance Vector routing protocol within a mobile environment. The analyses of these protocols are done by mean simulations which required Tool Command Language scripts. This script is an input file to Network Simulator and it contains different operations like scheduling, networking, connecting, and traffic and mobility parameters [32]. The script along with other files like traffic and mobility in conjunction will complete the particular simulation. Since traffic is not an issue of this research and so it is kept constant. The mobility is the major consideration and mobility files with different pause times are required for the particular set of simulation accordingly. All these mobility files are defined herein with definite parameters such as number of mobile nodes, area of simulation, time of simulation, and pause time in between nodes mobility. To identify an efficient and supported protocol set in Mobile Ad hoc Networks, each selected variant of transmission control protocol like New Reno, Sack and Vegas with common Mobile Ad hoc Network routing protocol will be specified in their respective Tool Command Language script. These script files will be further associated with traffic and mobility files and simulated by network simulator to generate an output file for every script file called trace files. The separate script file is processed with simulator that is being compiled by routing protocol. The simulator after processing each file will generate two different files. One for animation which is called network animator (NAM) and another for tracing output, called trace file. The network animator file consists of all the animated operations like nodes movement, connection establishment with data transfer, packets dropping, and overall nodes performance presented at the time of simulation. It also comprises of all the positioning and graphical information with their respective parameters. The trace file contains all the data statistics such as how many packets are sent, received, dropped and with what sequence number, their types, and sizes. The trace file is simply a log file of particular simulation with all the information logged in it. After getting the trace files, the ultimate task is to analyze those trace files and fetch the required information accordingly. There are various analyzing methods available, notably, PERL (Practical Extraction and Reporting Language), AWK (named after their writers, Alfred Aho, Peter Weinberger, and Brian Kernighan) and some text search software. This research work uses AWK scripts coding to analyze the trace files. The reasons for selecting these scripting is that, it contains simple c-language type coding with easy to use semantic statements for extracting and comparing the required parameters from the script files. AWK scripts can also be helpful in different calculations like throughput, packets dropping, and end-to-end delay. As soon as all the required information is fetched and calculated, the results can be displayed as an output and can also represented by graphs.
7. SIMULATIONS AND RESULTS
7.1 Simulation Parameters:
To perform the simulations in a manner to achieve the desired results, the simulation model was set that comprises of 50 mobile nodes with 10 connections in between them. These connections could be form and deform on ad hoc basis. The total time duration of every simulation is set to 700 seconds. Though this simulation time makes lengthy analysis but it is considered sufficient in correspondence with mobile nodes in wireless simulation. The boundary area for simulation is set to 1000 meters x 800 meters which is again a standard form for wireless simulations. Data packets can be exchanged between the nodes as they traverse within the hearing range of one another. The traversing speed is set to 20 meters/sec. As nodes move away due to mobility, link breaks and connection deformation occurred. In this situation, packets start getting dropped until Ad hoc On-demand distance vector routing protocol discovers any other suitable path(s). These common parameters applied to each simulation of different pause times. Pause times are required to hold the nodes when they reach at some particular position for specified time. The specified pause times selected for these simulations are: 10, 100, 250, 450, and 700 seconds for each three selected transmission control protocol variants. Each pause time scenario further contains seven different randomized generated mobility criteria for creating random positions of nodes. As a result, 35 trace files are generated for each transmission control protocol variant with total of 105 simulations. The tabulated forms of this description are concisely mentioned in Tables 1 through 4.
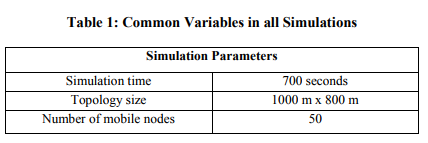
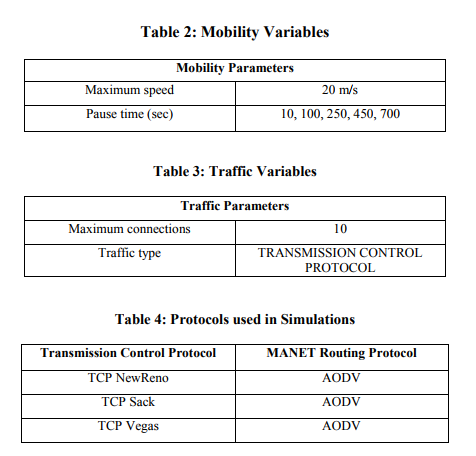
The common variables used for simulation purpose are simulation time, topology size, and mobile nodes. Mobile nodes demonstrate their operations in relation with the assigned values of parameters. The other factor is related with the demonstration area. The area of analyzing mobile nodes is specified by the provided region as a topology size which could be in x-axis and y-axis.
7.3 Simulation Results: The results generated after performing simulations with different parameters in trace files were analyzed with the help of AWK script. The comparable values in parameters are:
- Packet Delivery
- Rate Average End-to-End Delay
- Total Packets Dropped
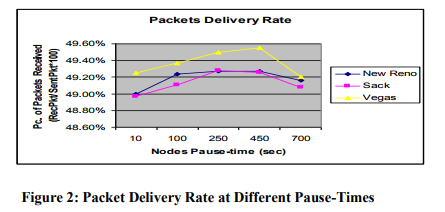
7.3.1 Packet Delivery Rate:
Packet delivery rate refers to the number of packets received by the destination at any particular time. Since this research concerns with transmission control protocol type of traffic, so the receptions of transmission control protocol are involved in the result. On analyzing the graph of packet delivery rate, results are shown in a close range of values i.e. 48.80% to 49.60%. The reason for this partial percentage values is the number of connection with respect to mobile nodes. In one perspective the given values could be thought at a constant linear rate; but in critical analysis, Vegas is continuously changing its delivery rate in an incremental structure from pause time 10 to 450. At pause time 700 where there is no mobility and nodes are in static position, delivery rate of packets suddenly slow down. The same case continues with New Reno and SACK having second and third place of performance respectively. The reason for delivery rate‘s decrement at pause time 700 is due to the absence of mobility in nodes. Hence, if no connection establishes in between source and destination for some particular time then there will be no increase in the delivery rate. The other point to ponder here is linked with the close values in percentage between all the transmission control protocol variants. This is because of the reliable nature of transmission control protocol and ts congestion control mechanism. The other important point is the convergence of protocol values at the same point when there is no mobility. This convergence fact again leads to the betterment of Vegas in different mobile scenarios than New Reno and SACK. But when there is no mobile environment, performance of all transmission control protocol variants is same.
7.3.2 Average End-to-End Delay:
The average end-to-end delay is defined as an estimated time required in sending packets from source node to the destination node. It is also defined as how much time it takes by packet to move from the sending node to the receiving node. The averaged results show that Vegas has very low and constant delay factor in comparison with New Reno and SACK at different pause times. The reason for this constant delay by Vegas is because of its better estimation approach and also its capability to detect any congestion in advance. Vegas attempts to keep the sending rate around a point estimated by the RTT samples. The idea is that if we increase the sending rate, and the RTT does not increase. However, if the RTT increases as we increase the sending rate, then we are not getting more bandwidth and instead are just taking up more space in the queues of intermediate than necessary [19]. The other variants such as New Reno and SACK have high delay factor and increases from one pause time to other, this delay factor is increased when nodes are at static position and no mobility is there.
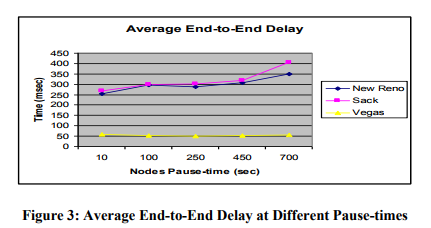
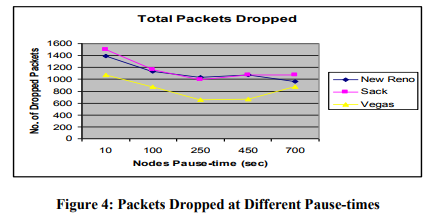
7.3.3 Total Packets Dropped:
The final evaluation aspect of this research is packet dropping. Wireless is a loose environment and especially Mobile Ad hoc Networks, where connection formation and deformation is usually more common. Packet dropping refers to the loss of packet due to connection unavailability or nodes are not in the range of each other. The graph shows low packet dropping with Vegas and Ad hoc On Demand Vector than other counterparts. The other thing to be noted is the level of dropping. The graph show high dropping when there is high mobility in all selected transmission control protocol variants and Ad hoc On Demand Vector, but have very nearer values of packets drop when nodes have no mobility i.e. they are on static positions. In all cases, the results are in favor of transmission control protocol Vegas better performance with Ad hoc On Demand Vector.
8. ANALYSIS AND EVALUATION
The graphical results obtained after rigorous simulations through Network Simulator-2 at different mobility scenarios with different parameters were analyzed using AWK scripts. The outcomes from these trace files show the clear and apparent comparison of transmission control protocol variants with Ad hoc On Demand Vector routing protocol. It has been noticed at different pause time intervals that the overall performance of Vegas with Ad hoc On Demand Vector routing protocol is more efficient. Transmission control protocol Vegas perform much better when detecting congestion due to its dominant congestion control algorithm which enables to infer congestion and/or any link failure before occurrence of such conditions as compare to other transmission control protocol variants. Vegas estimation approach is also much better as it calculates the round trip time (RTT) of each transmitted packet. If there is major difference in between any transmission of round trip time packets, then Vegas use congestion avoidance algorithm to get early cautious and prepare for session throttling. With these and many other advantages discussed earlier Vegas really shows a better performance in Mobile Ad hoc Network environment of mobility scenario than the other two standardized variants frequently implemented in wired networks. The overall performance of results as shown in appendix A is further being analyzed with -Weighted Evaluation Matrix? [1]. The evaluated results from this weighing matrix are shown in Table 5.
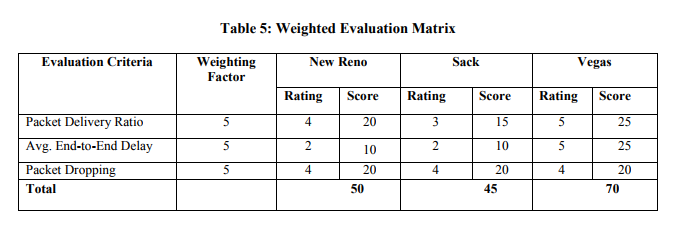
In the evaluation procedure, the weighting factor is assigned to each criterion. The value of this factor is set to ?5‘ for the entire considered criteria such as packet delivery rate, average end-to-end delay, and packets dropped. There is a quantitative rating to each qualitative value such as: poor, fair, good, very-good, excellent. These qualitative values again have their numerical values of 1, 2, 3, 4, and 5 respectively. The assignment of these values is done by characterizing the overall performance of results according to their output levels. After the weights are assigned to each category, calculations are performed. In calculation, the rating assigned from the results shown in Appendix A to each criterion of individual protocol set would be exploited. The weighing factors are multiplied with their corresponding assigned ratings to determine the operation score. At the end of each score, summation is performed to get the total result of every individual protocol pair (transmission control protocol and Ad hoc On Demand Vector). The pair with their scores in total will be assigned the ranking accordingly. The Weighted Evaluation Matrix comparatively demonstrates the analyzed results. The evaluated results in Table 5 visibly specify that Vegas have the highest score of ?70‘ on its performance. Secondly, New Reno was quarterly less than Vegas with the score of ?50'. Lastly, SACK has secured ?45' which is nearly half of the Vegas. Consequently in this study with certain protocol combinations, transmission control protocol Vegas has definitely better outcome in various scenarios of Mobile Ad hoc Network with mobility than New Reno and Sack.
CONCLUSIONS AND FUTURE WORK
In this paper the performance of different transmission control Protocol variants with Ad hoc On Demand Vector routing protocols was discussed and argued on the basis of simulations and their results. The extensive and rigorous simulations under a range of various operative parameters of mobility were performed. The ultimate outcomes of the analyzed results have proved clearly the suitable simulation of the required protocols combination. The preferable combination of protocols with this study comprises of transmission control Protocol variant Vegas with Ad hoc On Demand Vector routing protocol. In comparison with the results of other studies performed in different simulation scenarios, Vegas always have an above average performance. The overall highest score according to the evaluation method of this study is ?70?, and it was obtained by Vegas. The future work could be conducted with the analysis of Mobile Ad hoc Network environment under different quality of service issues like nodes energy consumptions, issues of hidden and exposed terminal, and constraints in mobility and traffic criteria. Also due to the unavailability of transmission control protocol Westwood in Network Simulator 2, it was not included in the simulation process and in analysis study. Though, researchers are working on the availability of Westwood in Network Simulator 2, downloading periodically updated manual available at [32] could be helpful in this regard and in future analyses considerations
References:
1. AWAD, E.M., (1993) System Analysis and Design, Galgotia Publications (P) Ltd, 524 pp
2. BASAGNI, S., CONTI, M., GIORDANO, S., and IVAN, G., (2004) Mobile Ad Hoc Networking, IEEE Press, 480 pp
3. B. JYE CHANG, S. YU, LIN, Y. HSIN and LIANG; TCP Taichung: a RTT-based predictive bandwidth based with optimal shrink factor for TCP congestion control in heterogeneous wired and wireless networks, Proceedings of international conference on Embedded and ubiquitous computing, December, 2007
4. BRAKMO, S.L., O‘MALLEY, W.S., and PETERSON, L.L. (1998) TCP Vegas: New Techniques for Congestion Detection and Avoidance. Department of Computer Science, University of Arizona, Tucson, AZ
5. CHEN, T.S., CHIH, Y.C., and YUH, S.C. (2005) Wireless Ad Hoc and Sensor Networks Journal of Internet Technology, Vol. 6, No. 1
6. COMER, D.E., (2001) Computer Networks and Internet with Internet applications, 3rd ed., Prentice Hall, 683 pp
7. COMPUTER MAGAZINE, Institute of Electrical and Electronic Engineering (IEEE) Press. Issue February 2004
8. FLOYD, S., HENDERSON, T., and GURTOY, A. (2004) The NewReno Modification to TCP‘s Fast Recovery Algorithm. Request for Comments: 3782
9. FOROUZAN, B.A., (2000) Data Communications and Networking, 2nd ed., McGraw-Hill, 908 pp
10. GERLA, M. (2004) Official web site of High Performance Internet http://www.cs.ucla.edu/NRL/hpi/, accessed n 17-6-2006.
11. GRIECO, L.A., and MASCOLO, S. (2004) Performance Evaluation and Comparison of Westwood+, New Reno, and Vegas TCP Congestion Control. Dipartimento di Elettrotecnica ed Elettronica, Politecnico di Bari, Italy
12. HALDAR, P. (2002) Wireless World in NS. USC/ISI. http://www.isi.edu/nsnam/ns/nstutorial/tutorial-02, accessed 8-6-2002.
13. HENGARTNER, U., BOLLIGER, J., and GROSS, T. (2000) TCP Vegas Revisited.Departement Informatik, ETH Z¨urich, CH 8092 Z¨urich
14. H. BALAKRISHNAN, S. SESHAN, AND R. H. KATZ, -Improving reliable transport and handoff performance in cellular wireless networks,? ACM Wireless Networks, vol. 1, Dec. 1995
15. HOLLAND, G., and VAIDYA, N. (2002) Analysis of TCP Performance over Mobile Ad Hoc Networks. DCS, Texas Aand M, College Station, TX, and Department of Electrical and Computer Engineering, University of Illinois at Urbana-Champaign, Urbana, IL, USA, respectively
16. IETF MANET GROUP: http://www.ietf.org/html.charters/manetcharter.html, accessed on 23-4-2006.
17. JACOBSON, V. (1990) Transmission Control Protocol (TCP) Congestion Control. Request for Comments: 2581
18. JENS-PETER REDLICH (2004). System Architecture Group. Computer Science Department Humboldt University Berlin/Germany http://sar.informatik.huberlin.de/teaching/_previous-years/2004- w%20Ad-Hoc%20Networks/presentations /021-NetworkSimulator_ns2.pdf accessed on 12-3-2006.
19. JONG, S.A., PETER, B.D., ZHEN, L., and LIMIN, Y. (1995) Evaluation of TCP Vegas: Emulation and Experiment Computer Science Department, University of Southern California, Los Angeles, CA
20. JEONGHOON, M., RICHARD J.L., VENKAT, A., and JEAN, W. (1998) Analysis and Comparison of TCP Reno and Vegas, Department of Electrical Engineering and Computer Science, University of CaliFornia at Berkeley
21. KAZI, W. (2005) GATEWAY SELECTION BASED ON GATEWAY LOAD IN AD HOC INFRASTRUCTURED ENVIRONMENT. MS thesis, Asian Institute of Technology, Thailand
22. KUROSE, J.F., and ROSS, K.W. (2004) Computer Networking: A Top Down Approach Featuring The Internet, 3rd ed., Addison Wesley, 821 pp
23. LANG, D. (2003) A Comprehensive Overview About Selected Ad Hoc Networking Routing Protocols, DCS, Technische Uni. Munich, Germany, pp. 47
24. PERKINS, C., BELDING, E., and DAS, S. (2003) Ad hoc On- Demand Distance Vector (AODV) Routing. Request for Comments: 3561
25. R. Yavatkar and N. Bhagwat, -Improving end-to-end performance of TCP over mobile internetworks? in Mobile 94 Workshop Mobile Computing Syst. Appl. Dec. 1994
26. RUY, D.O., and BRAUN, T. (2002) TCP in Wireless Mobile Ad Hoc Networks, Institute of CS and Applied Mathematics, University of Berne, Switzerland
27. S. Floyd, -HighSpeed TCP for Large Congestion Windows,? RFC 3649, December 2003
28. SESHAN, S. (2001) Computer Networking. Lecture 19 – TCP Performance, Carnegie Mellon University
29. SHEWTA, S. (1998) ?A TCP Tutorial‘. Available at http://www.ssfnet.org/Exchange/tcp/tcpTuto rialNotes.html, accessed on 25-8-2004
30. VENKATESH, R., and MIGUEL, A.L. (2002) Performance Analysis of TCP over Static Ad Hoc Wireless Networks. Department of CS and Engineering, University of South Florida Tampa, FL, USA
31. TANENBAUM, A.S., (2002) Computer Networks, 4th ed., Prentice Hall, 891 pp.
32. VINT Project (2005), ?The NS Manual‘ formerly NS document, Available at http://www.isi.edu/nsnam/ns/nsdocumentation.html, accessed on 14-9-2007.
|






 This work is licensed under a Creative Commons Attribution-NonCommercial 4.0 International License
This work is licensed under a Creative Commons Attribution-NonCommercial 4.0 International License